Enable Malware Protection For S3
Enable New Feature
Find and access the Amazon GuardDuty service
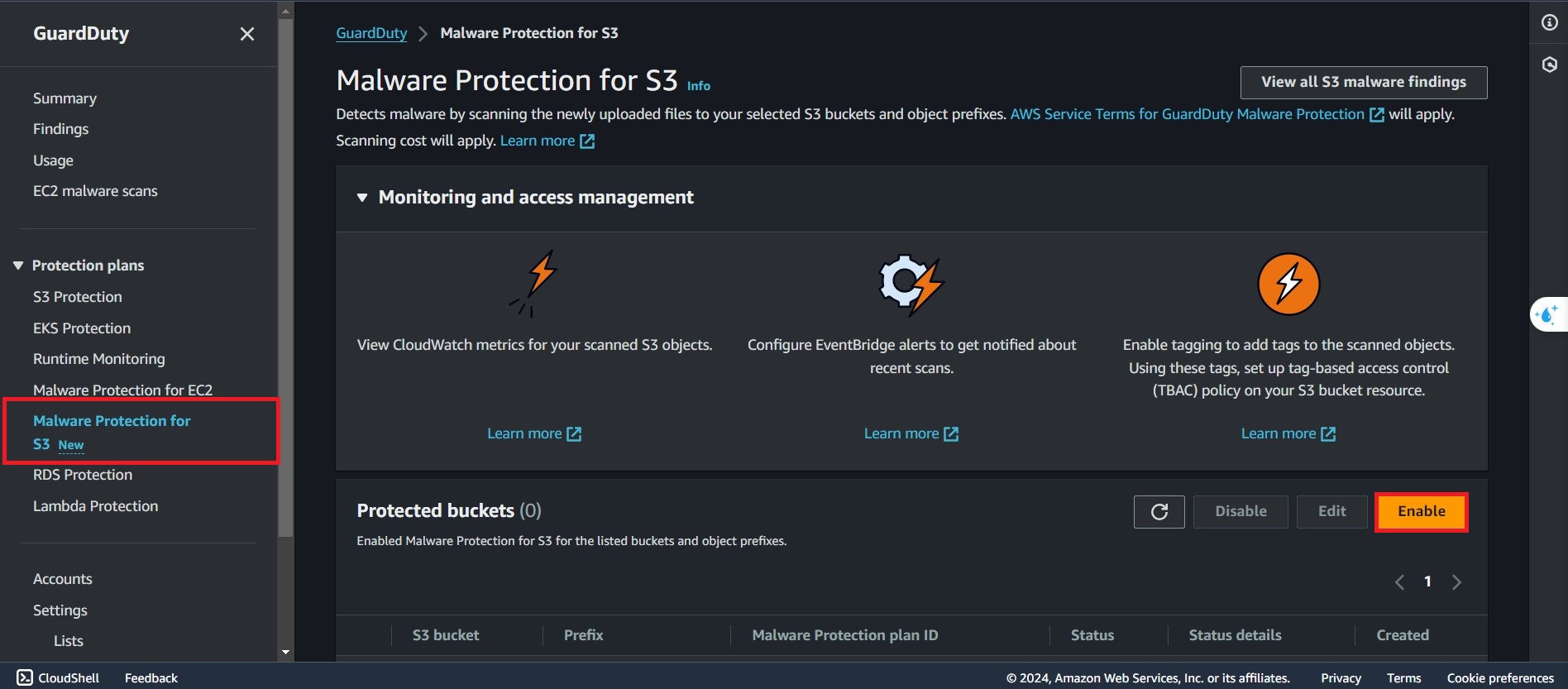
Select the S3 bucket that need protection
You can choose Object with a specific prefix in order to custom prefix file in your bucket. In this project, we will scan all the files that in the bucket.
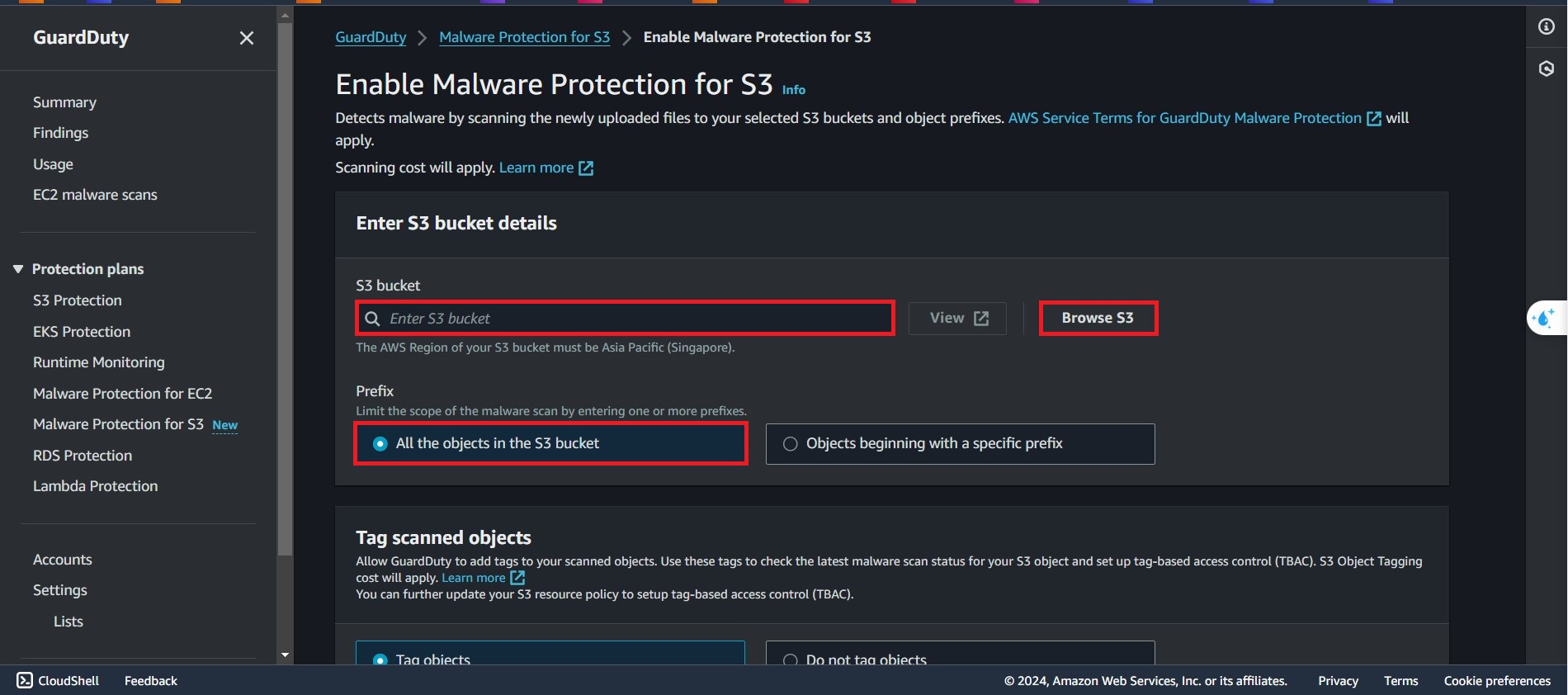
Choose the
s3-raw-gdoptions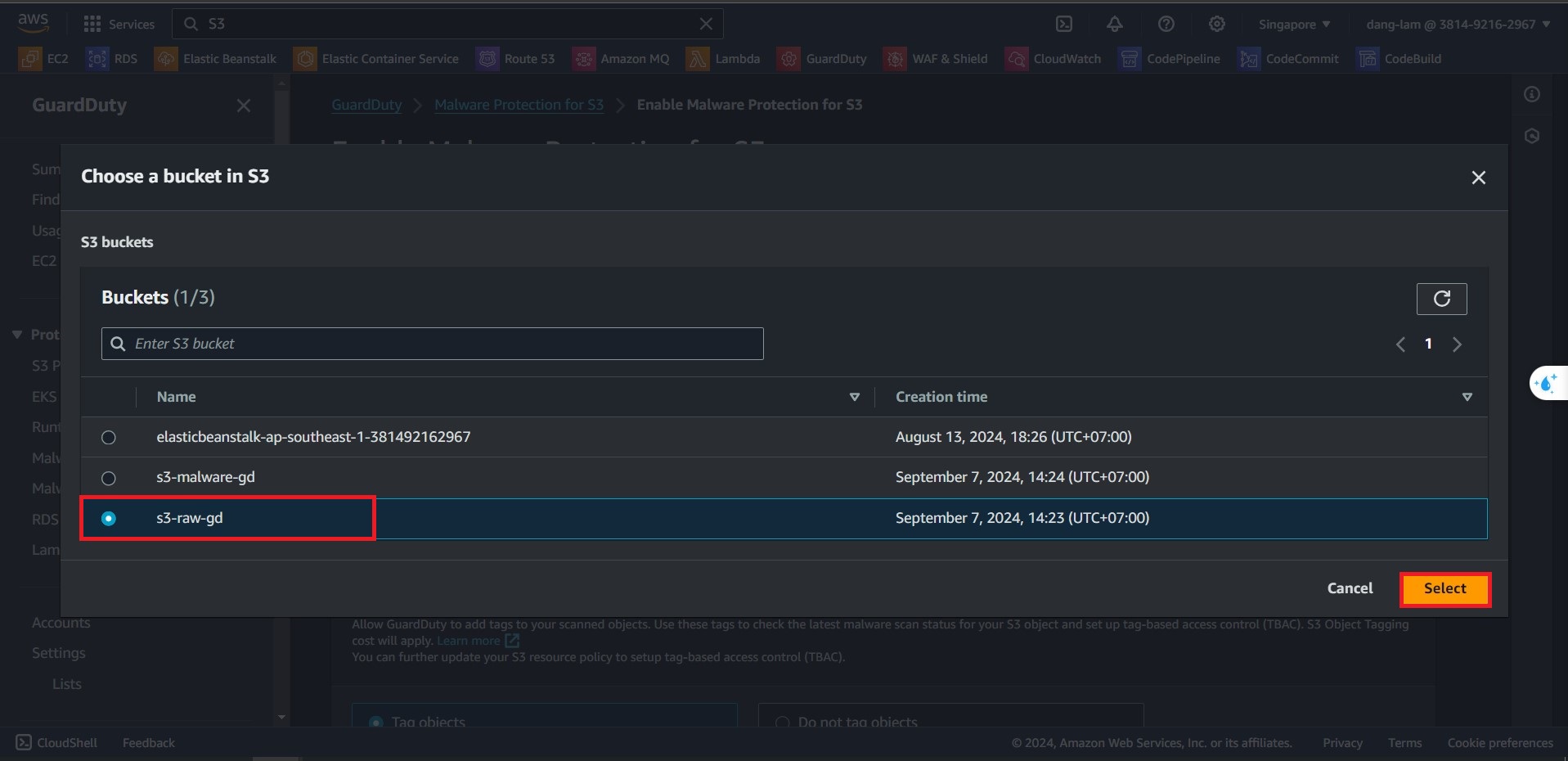
In the Tag Scan Object section:
- choose Tag Objects: this allow GuardDuty write scan status into tag section in S3 Objetcs
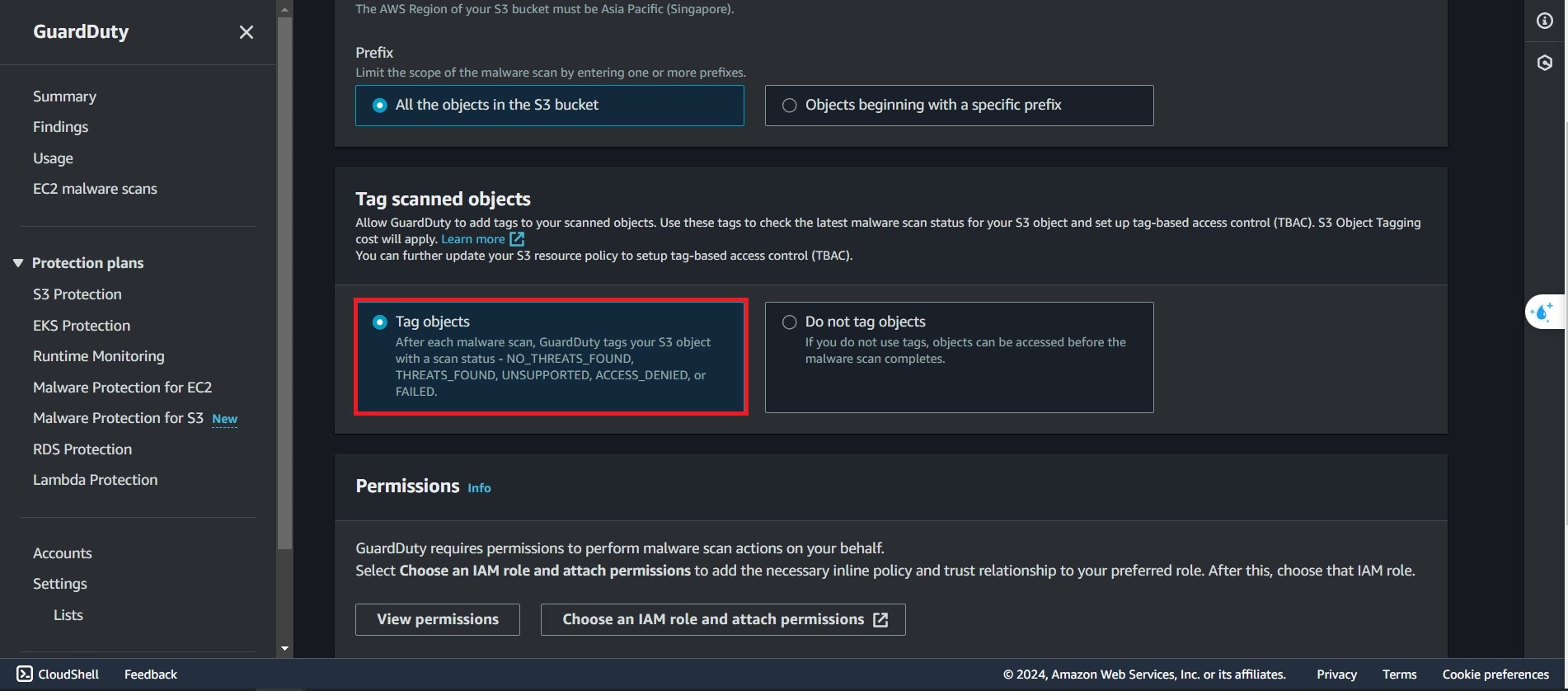
- choose Tag Objects: this allow GuardDuty write scan status into tag section in S3 Objetcs
In the Permission section, review the Policy and Trust Relationship.
Policy
{ "Version": "2012-10-17", "Statement": [ { "Sid": "AllowManagedRuleToSendS3EventsToGuardDuty", "Effect": "Allow", "Action": [ "events:PutRule", "events:DeleteRule", "events:PutTargets", "events:RemoveTargets" ], "Resource": [ "arn:aws:events:ap-southeast-1:381492162967:rule/DO-NOT-DELETE-AmazonGuardDutyMalwareProtectionS3*" ], "Condition": { "StringLike": { "events:ManagedBy": "malware-protection-plan.guardduty.amazonaws.com" } } }, { "Sid": "AllowGuardDutyToMonitorEventBridgeManagedRule", "Effect": "Allow", "Action": [ "events:DescribeRule", "events:ListTargetsByRule" ], "Resource": [ "arn:aws:events:ap-southeast-1:381492162967:rule/DO-NOT-DELETE-AmazonGuardDutyMalwareProtectionS3*" ] }, { "Sid": "AllowPostScanTag", "Effect": "Allow", "Action": [ "s3:PutObjectTagging", "s3:GetObjectTagging", "s3:PutObjectVersionTagging", "s3:GetObjectVersionTagging" ], "Resource": [ "arn:aws:s3:::<bucket_name>/*" ] }, { "Sid": "AllowEnableS3EventBridgeEvents", "Effect": "Allow", "Action": [ "s3:PutBucketNotification", "s3:GetBucketNotification" ], "Resource": [ "arn:aws:s3:::<bucket_name>" ] }, { "Sid": "AllowPutValidationObject", "Effect": "Allow", "Action": [ "s3:PutObject" ], "Resource": [ "arn:aws:s3:::<bucket_name>/malware-protection-resource-validation-object" ] }, { "Effect": "Allow", "Action": [ "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::<bucket_name>" ] }, { "Sid": "AllowMalwareScan", "Effect": "Allow", "Action": [ "s3:GetObject", "s3:GetObjectVersion" ], "Resource": [ "arn:aws:s3:::<bucket_name>/*" ] }, { "Sid": "AllowDecryptForMalwareScan", "Effect": "Allow", "Action": [ "kms:GenerateDataKey", "kms:Decrypt" ], "Resource": "arn:aws:kms:ap-southeast-1:381492162967:key/<key_id>", "Condition": { "StringLike": { "kms:ViaService": "s3.*.amazonaws.com" } } } ] }Trusted Relationship:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Service": "malware-protection-plan.guardduty.amazonaws.com" }, "Action": "sts:AssumeRole" } ] }
Make sure to save both the permissions details for later, and then continue to the next parts.