Create Event for GuardDuty
Overview
In this section, we will implement an event-driven architecture to monitor findings from Amazon GuardDuty in real time. Using Amazon EventBridge, we will create rules that trigger specific actions whenever GuardDuty detects potential threats or vulnerabilities
In the AWS search bar, type EventBridge and select the first one.
Switch to the EventBridge Rule tab and click Create Rule
Type
rule-event-gdfor the Name section, and leave the default option for the rest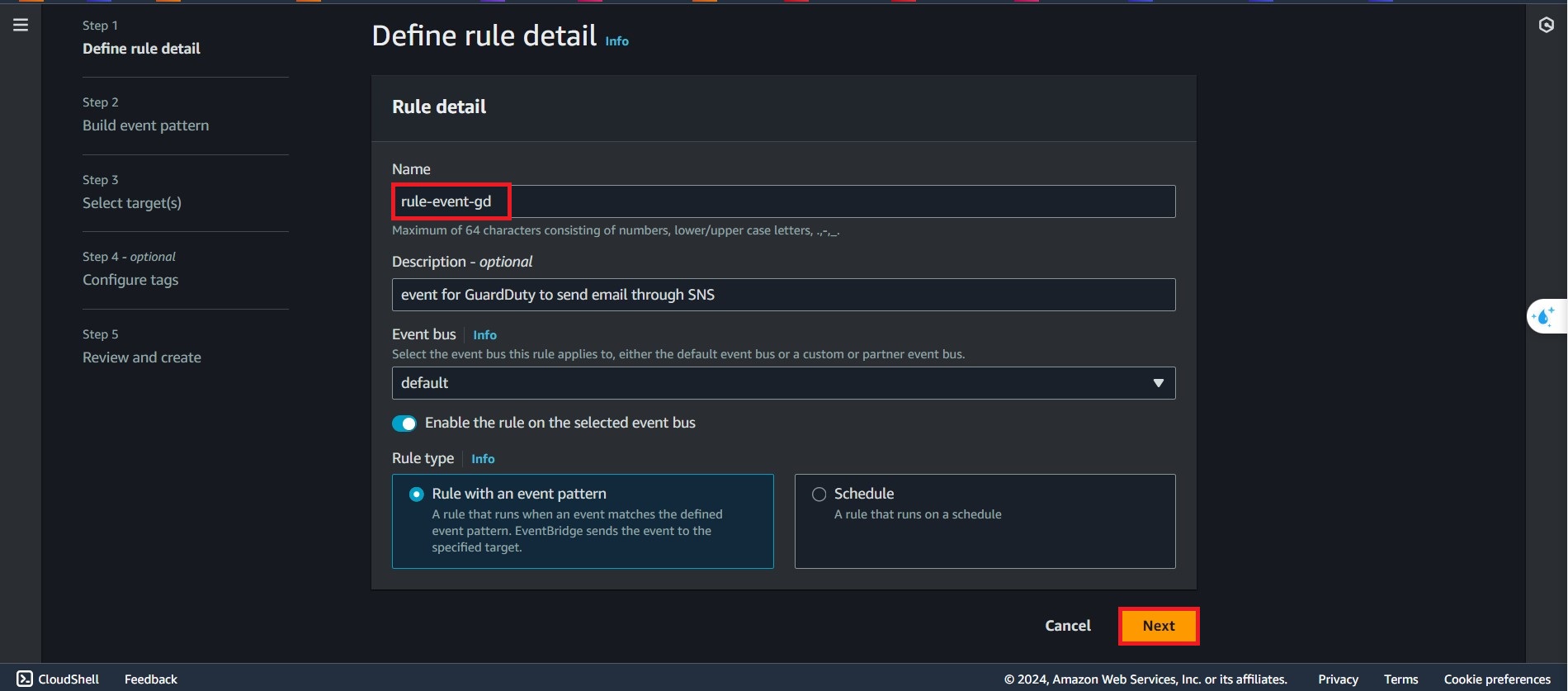
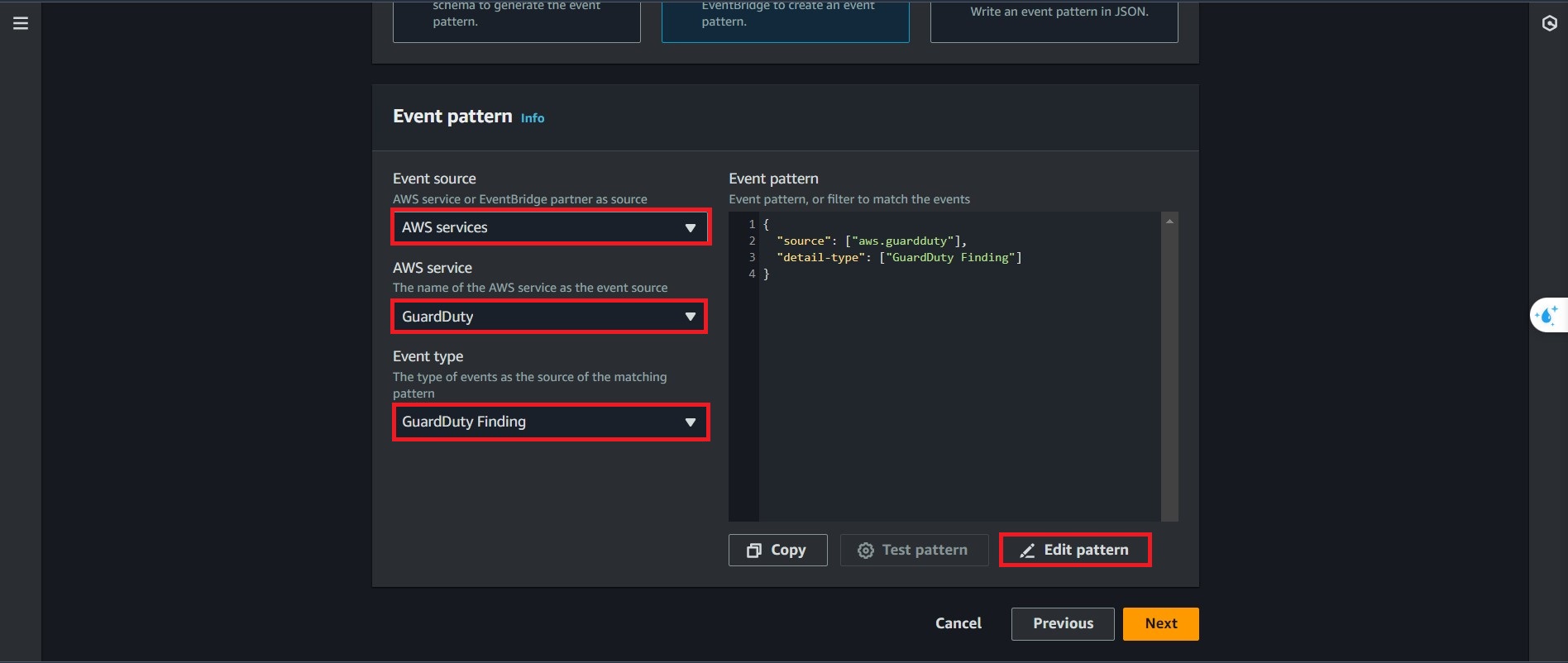
On the Event Pattern, select the following
- Event Source, Select AWS service
- Choose GuardDuty for AWS service
- GuardDuty Findings for the event type.
Then, choose the Edit Pattern to change the servity of the event will be triggered.
Paste the following and modify the dangerous level of the findings
{ "source": [ "aws.guardduty" ], "detail-type": [ "GuardDuty Finding" ], "detail": { "severity": [ 4, 4.0, 4.1, 4.2, 4.3, 4.4, 4.5, 4.6, 4.7, 4.8, 4.9, 5, 5.0, 5.1, 5.2, 5.3, 5.4, 5.5, 5.6, 5.7, 5.8, 5.9, 6, 6.0, 6.1, 6.2, 6.3, 6.4, 6.5, 6.6, 6.7, 6.8, 6.9, 7, 7.0, 7.1, 7.2, 7.3, 7.4, 7.5, 7.6, 7.7, 7.8, 7.9, 8, 8.0, 8.1, 8.2, 8.3, 8.4, 8.5, 8.6, 8.7, 8.8, 8.9 ] } }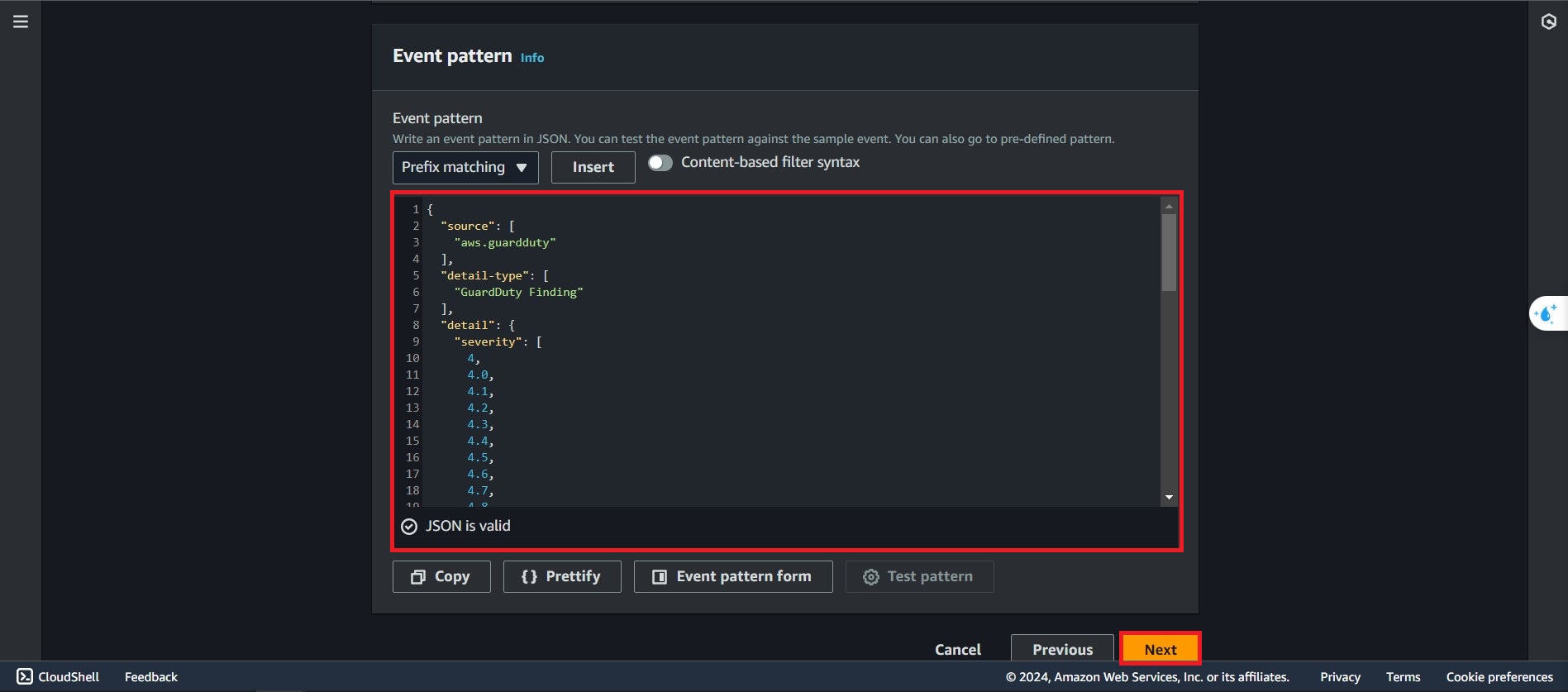
In the Advance Settings, Select the below:
- Choose AWS service
- Select SNS topic
- and in the Topic part, choose the
guardduty-topic, that you just created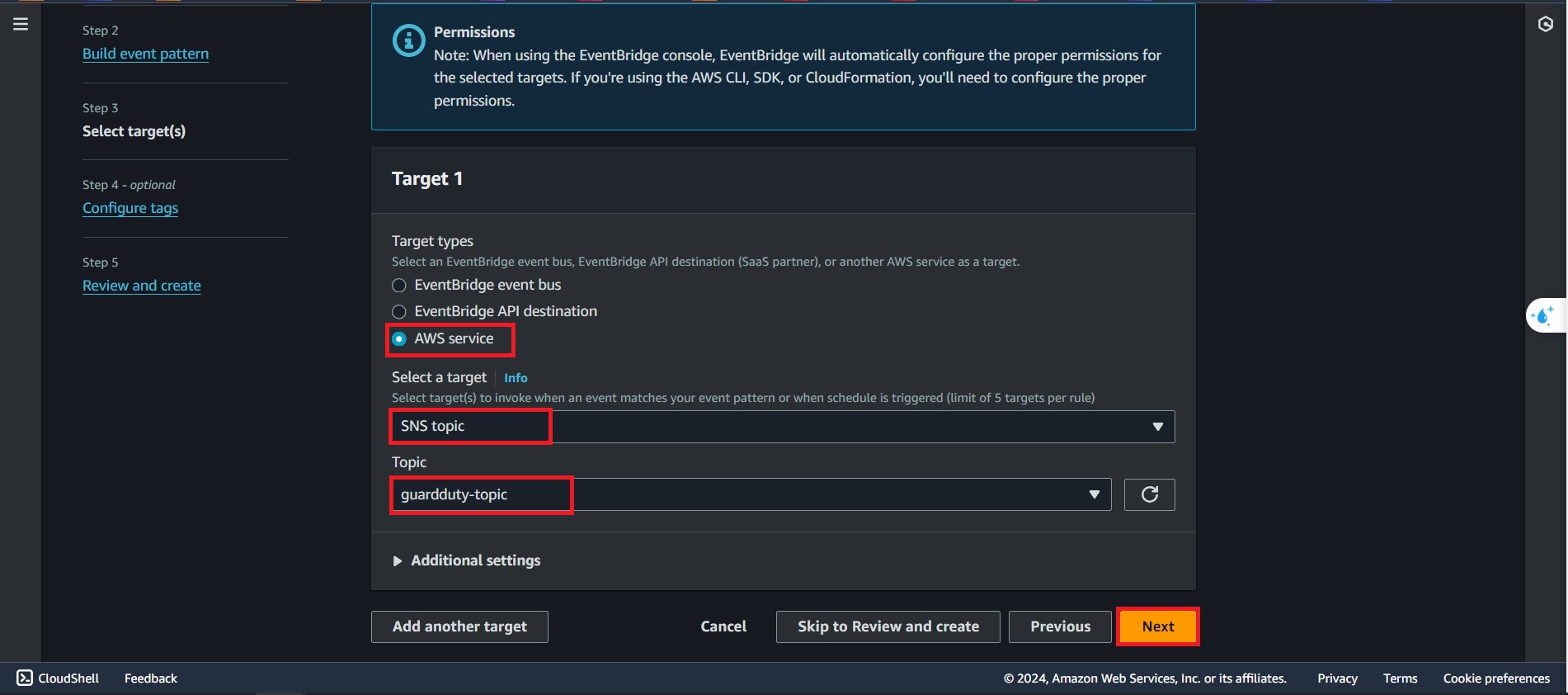
Next, we will create a custom notification for SNS:
- In the additional settings, select Input transformer
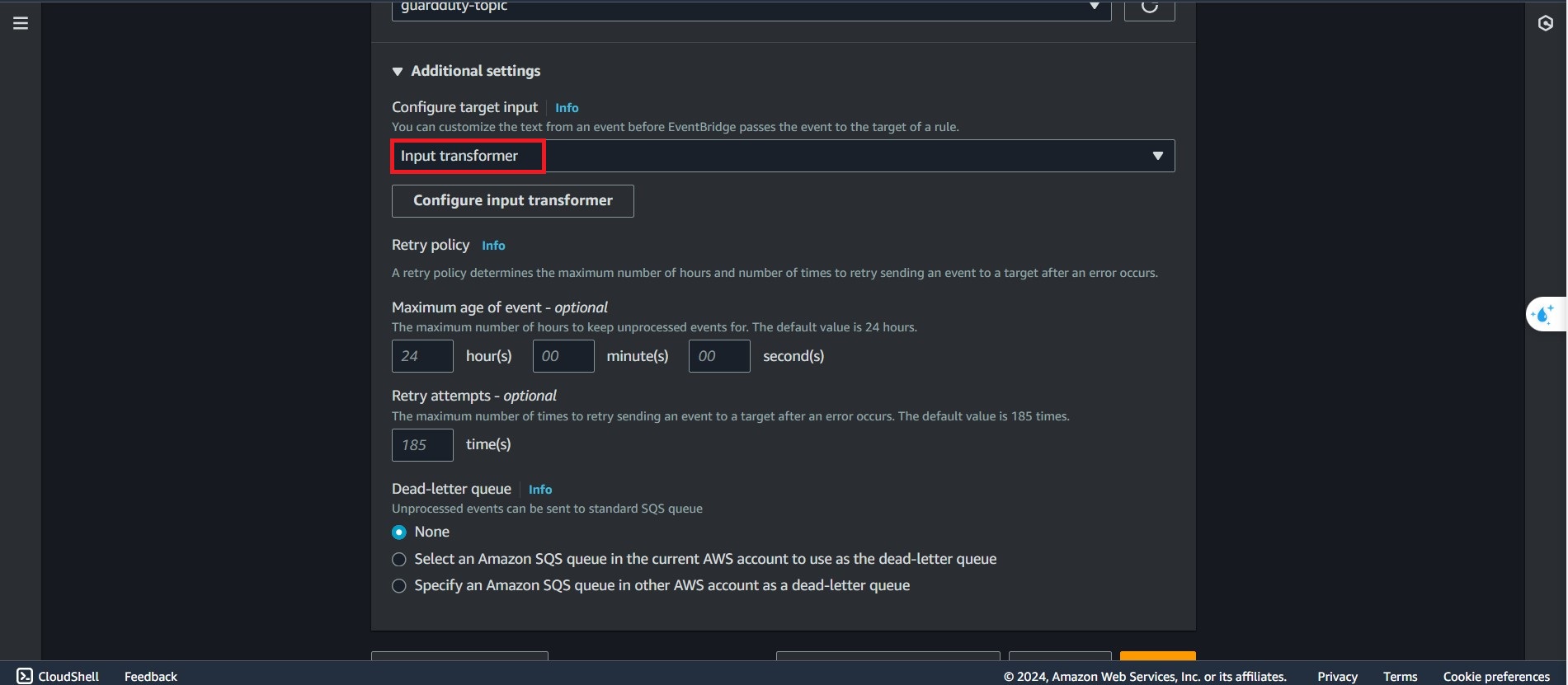
- In the additional settings, select Input transformer
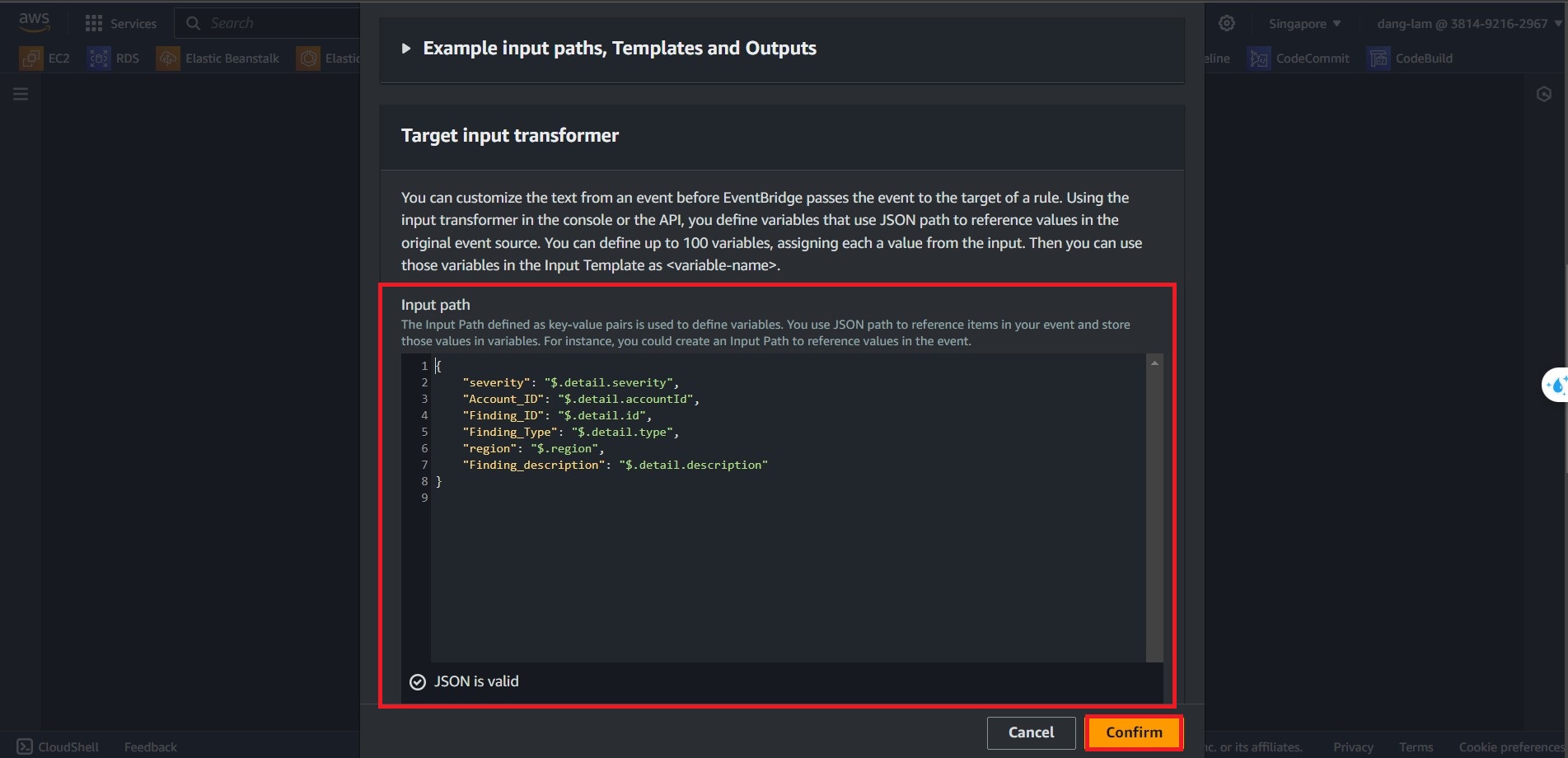
In the Target input transformer, Type the following Input Path:
{ "severity": "$.detail.severity", "Account_ID": "$.detail.accountId", "Finding_ID": "$.detail.id", "Finding_Type": "$.detail.type", "region": "$.region", "Finding_description": "$.detail.description" }
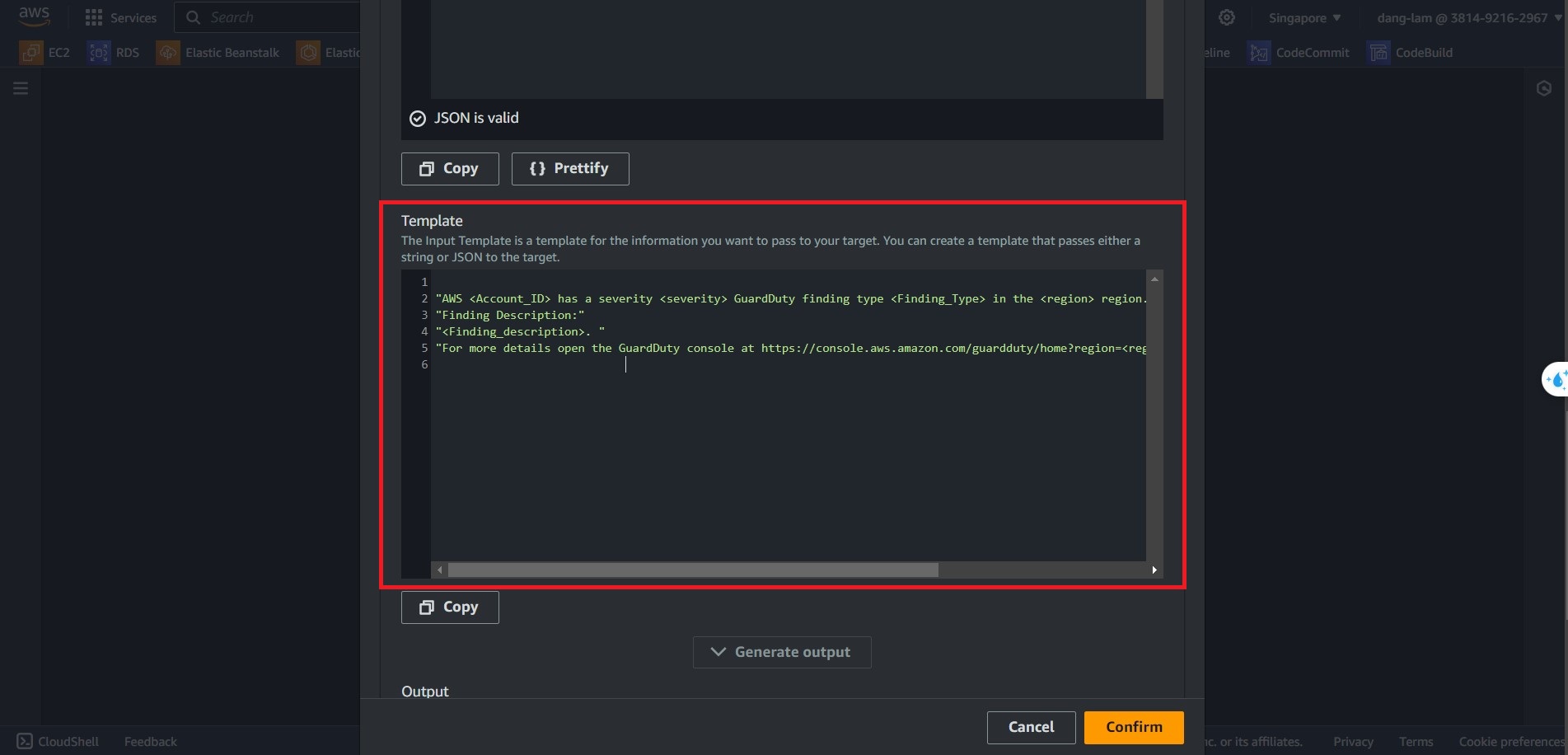
 9. On the Template, we will procvide the following Input Template:
9. On the Template, we will procvide the following Input Template:
"AWS <Account_ID> has a severity <severity> GuardDuty finding type <Finding_Type> in the <region> region."
"Finding Description:"
"<Finding_description>. "
"For more details open the GuardDuty console at https://console.aws.amazon.com/guardduty/home?region=<region>#/findings?search=id%3D<Finding_ID>"
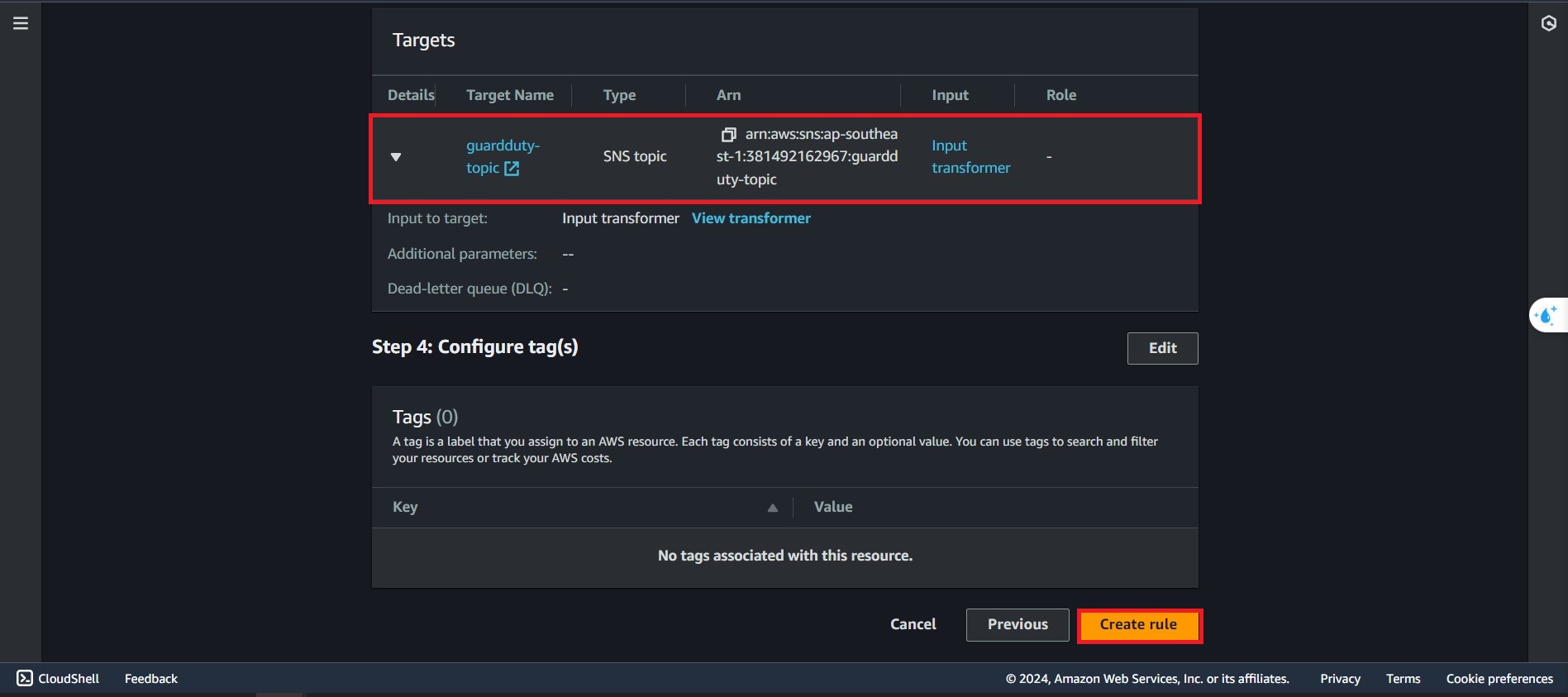
 10. Review and click Create rule
10. Review and click Create rule
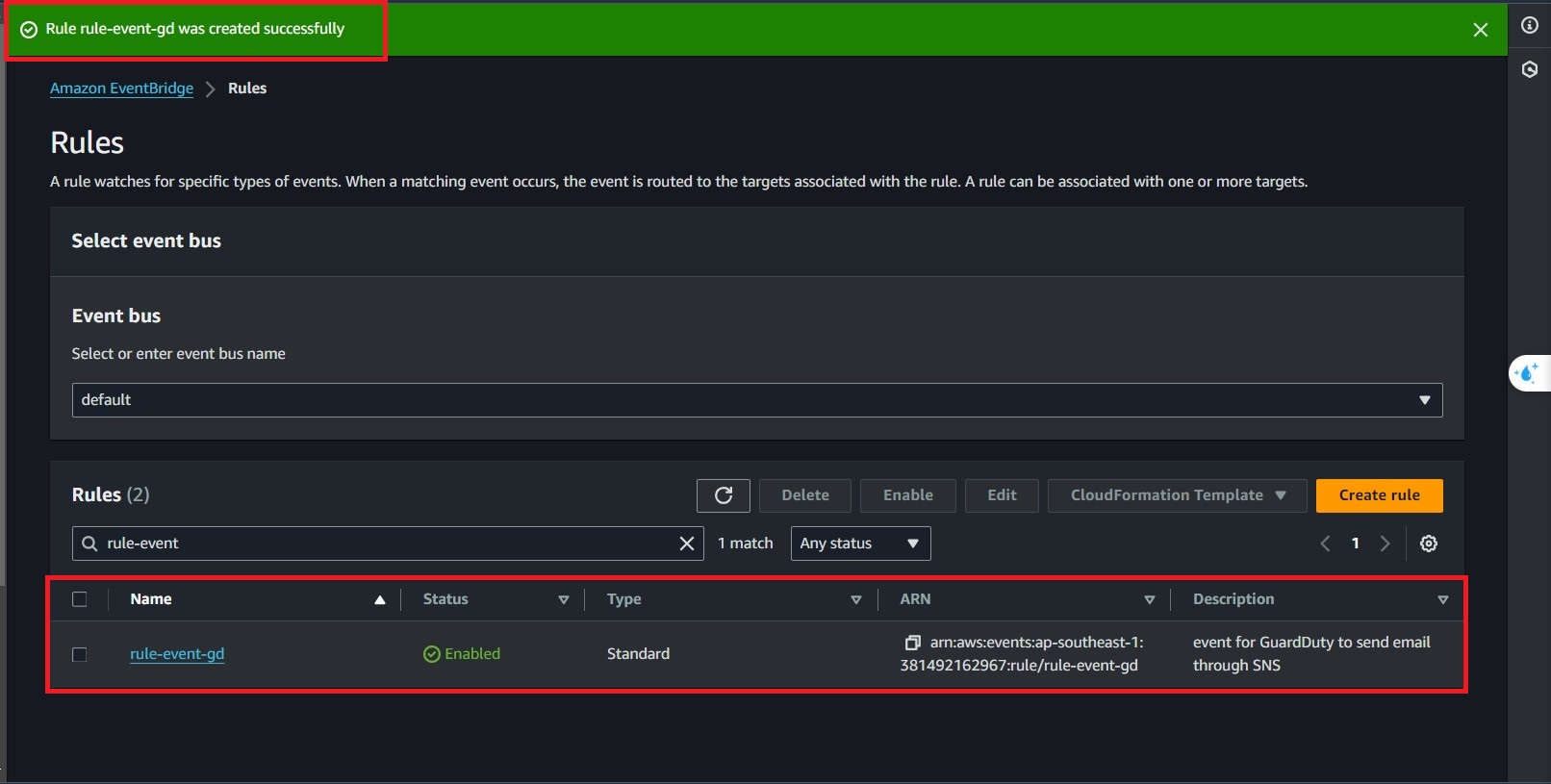
 11. Complete create event rule.
11. Complete create event rule.